
The A-Z of Cybersecurity Compliance Frameworks
What Is Cybersecurity Compliance?
Cybersecurity compliance refers to ensuring adherence with all relevant cyber regulatory requirements and national and state-level cyber laws undertaken by a specific enterprise to safeguard the sensitive information it processes in conducting business. In simpler terms, cybersecurity is merely the act of securing one's cyberspace, whereas compliance is the documentation of said actions in a standard format.
Cybersecurity compliance has become something of a hot topic in recent times thanks to the sudden spike in digitization that swept the world in the wake of the pandemic.
Cybersecurity compliance has been steadily gaining a place in mainstream discourse due to the overwhelming impact that technology has on our lives. Facebook's admission to mishandling the data of over 50 million users in the infamous Facebook-Cambridge Analytics data scandal turned the spotlight on customer privacy and the flippant attitude with which major tech companies handled sensitive information.
The implementation of the General Data Protection Regulation (GDPR) by the European Parliament ushered in a new era for cybersecurity compliance as technology companies scrambled to win the confidence of their customers and regulators. Cybersecurity compliance is now seen as a strategic imperative for companies that are serious about doing business.
What Is A Cybersecurity Compliance Framework?
Despite all the fanfare surrounding it, cybersecurity compliance is still an area of confusion for many business leaders simply due to the sheer diversity in business conditions and data types that companies end up processing. Different industries and different regions impose sets of controls on their business entities that collectively represent a fully functional cybersecurity program which can exacerbate this confusion. These controls constitute a cybersecurity compliance framework.
There is no one-size-fits-all solution when it comes to cybersecurity compliance frameworks. Each industry is unique and handles customer data differently.
For this reason alone, there are multiple frameworks, and most businesses end up using more than one framework depending on the kind of industries and regions they operate in.
To understand the different kinds of compliance frameworks that bind operations for companies that handle customer data, one must first understand the data subject to these frameworks. Critical data can be grouped under three major buckets: Personally Identifiable Information (PII), Protected Health Information (PHI), and Financial Information.
It must also be noted that the compliance landscape is starting to shift from implementing control-based requirements to risk-based requirements, which has triggered a worldwide metamorphosis in the kind of compliance frameworks that exist.

What Are The Different Cyber Security Frameworks?
NIST Cybersecurity Framework
The National Institutes of Standards and Technology (NIST), a non-regulatory agency of the United States Department of Commerce, introduced the eponymously named NIST Cybersecurity framework in 2014. Initially designed for the benefit of private sector organizations in the United States, the NIST Cybersecurity framework is centered around five essential functions, namely:
- Identify
- Protect
- Detect
- Respond
- Recover
The NIST Cybersecurity Framework is one of the broadest frameworks provided by the NIST and applies to almost any organization seeking to build a cybersecurity program.
IASME Governance
Envisioned by the Information Assurance for Small and Medium Enterprises (IASME) Consortium, the IASME Governance standard was meant to be an affordable and accessible alternative to the ISO/IEC 27001 standard.
IASME is unique because it originated as a partnership between British academics and Small/Medium Enterprises (SMEs) and is best suited for small businesses' cybersecurity needs.
Apart from covering Data protection (through GDPR), it also covers risk management, cloud services, malware protection, vulnerability scanning, incident management, firewalls, security policy, business continuity, amongst other crucial topics.
COBIT
COBIT (Control Objectives for Information and Related Technologies) is a framework created by the ISACA for IT management and governance. A highly process-oriented framework, COBIT's approach links business and IT goals together to delineate IT and Business teams' responsibilities.
COBIT identifies and advocates five processes: Evaluate, Direct and Monitor (EDM), Align, Plan and Organise (APO), Build, Acquire and Implement (BAI), Deliver, Service, and Support (DSS); Monitor, Evaluate and Assess (MEA).
COBIT was designed to cater to three objectives: legal compliance, increased agility, increased earning potential.
COSO
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) is different from other cybersecurity frameworks because it is more holistic and targeted towards eliminating corporate fraud. Since COSO comprises mainly auditing and accounting bodies, the COSO framework is built upon the process of 'Internal control,' a broad concept in accounting that relates to organizational risk management.
The COSO Internal Control framework contains five interrelated components, which are self-explanatory: Control Environment, Risk assessment, Control activities, Information and Communication, Monitoring.
TC CYBER
TC Cyber is the Technical Committee (TC) Cyber Division, one of many technical groups operating under ETSI (European Telecommunications Standards Institute). ETSI's activities are geared towards supporting the development and testing of standards for ICT-enabled systems.
ETSI TC Cyber's focus on security has led the organization to work on multiple security aspects, each with a set of standards. Their work is split across nine areas: Protection of personal data and communication, enterprise/individual cybersecurity, cybersecurity tools, EU legislative support, forensics, and quantum-safe cryptography.
CISQ
Consortium for IT Software Quality (CISQ) is a joint endeavor between Carnegie Mellon University's Software Engineering Institute (SEI) and the Object Management Group (OMG), a standards consortium.
CISQ's international standards to automate software quality measurement and the proliferation of secure, reliable, and trustworthy software are built around three areas of the source code: software size, structural quality, and technical debt.
CISQ's software security standard comprises 74 critical coding and architectural weaknesses to avoid in source code.
FedRAMP
Federal Risk and Authorisation Management Program (FedRAMP) is a set of standardized approaches to security assessment, authorization, and continuous monitoring, specifically for cloud products and services. It was introduced by the U.S government and is now used across all of its executive departments and agencies.
FedRAMP utilizes the NIST SP-800, and cloud service providers (CSPs) must undertake an independent security assessment by a third-party organization mainly to ensure the Federal Information Security Management Act (FISMA).
FISMA
The Federal Information Security Management Act (FISMA) is a federal law implemented by the United States Congress and was one of the earliest proponents of identifying information security as a critical objective to be realized by all its federal agencies.
FISMA's compliance framework advocates that all information systems used by federal agencies ought to be subject to. These are:
- Information Systems Inventory
- Risk Level Categorization
- Security controls
- Risk Assessment
- System Security plan
- Certification and Accreditation
- Continuous Monitoring
SCAP
The Security Content Automation Protocol (SCAP) refers to a set of interoperable specifications used to enable automated vulnerability management, measurement, and the level of policy compliance of information systems deployed within organizations.
SCAP provides several open standards which are used to enumerate software flaws and configuration issues concerning security. These standards are used when measuring systems to find vulnerabilities and identify them to evaluate the possible impact.

Benefits of Cybersecurity Compliance
Having robust cybersecurity compliance measures in place can benefit companies in many ways. From building a solid reputation with customers, staying on the right side of regulators, adhering to applicable laws, and the reigning compliance standards. Taken together, this is sure to contribute to the ease of doing business in the long run.
Ultimately, it is a means for a company to build a fortress around its operations. This means that companies need to invest in cybersecurity solutions from an existential perspective, especially in light of the increasing incidences of data breaches. Global spending on cybersecurity is estimated to reach $400Bn by 2025.
In its 2020 Data Breaches investigations report, Verizon uncovered some particularly worrying trends. A whopping 72% of breaches involved prominent business victims, and over 58% of them had their details compromised. 86% of these breaches were financially motivated, and nearly 70% of them were perpetrated by external actors, half of which were organized criminal groups, highlighting just how important it is to have robust cybersecurity governance and compliance in place.
Besides guarding against external threats, the implementation of cybersecurity compliance is a net positive for all the stakeholders:
- Businesses are seen as more trustworthy and ethical.
- Operational efficiency is bound to increase.
- A visible commitment to security can serve as a veritable competitive advantage.
Most companies tend to overestimate their existing cybersecurity capabilities, and the pandemic showed just how underprepared many businesses were. The first quarter of 2020 alone witnessed over 8.4 billion record breaches, a figure which ballooned to 37 billion by the end of the year. Implementation of solid cybersecurity governance and compliance disciplines is the best way to achieve overall resilience amongst businesses.
Cybersecurity is no longer an opportunity and is rapidly becoming necessary as companies begin to realize its strategic importance.
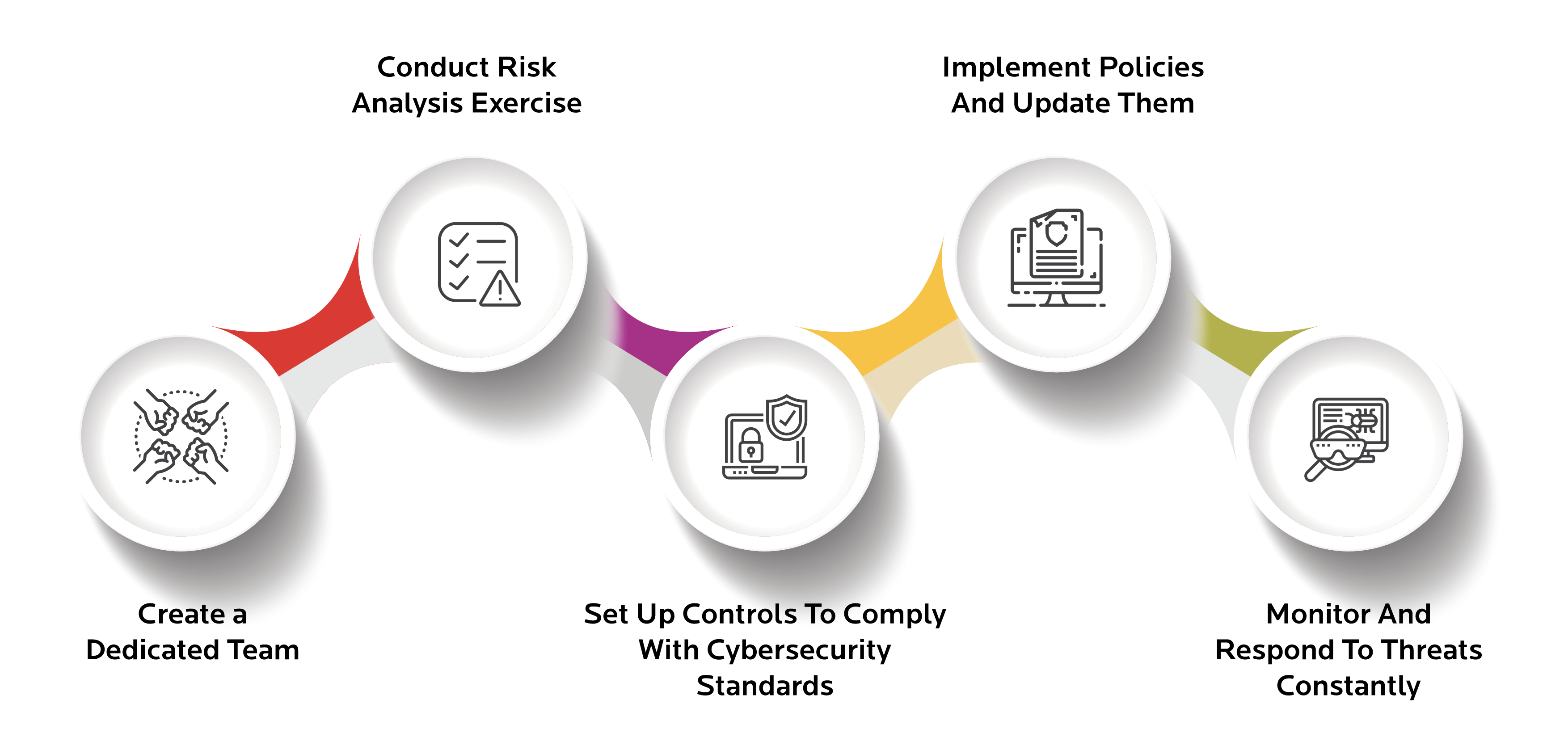
How To Build Your Cybersecurity Compliance Plan
The first step to putting a compliance plan together is to create a dedicated team whose sole purpose is to assess and monitor cybersecurity. These teams cannot operate in silos and must be established as an interdepartmental capability to ensure that their activities align with all the business and IT needs and workflows across the organization.
After creating a team, senior leaders within the organization will have to conduct a risk analysis exercise. Apart from identifying what the company is legally required to protect, companies will have to identify all information assets, systems, data, and networks that keep the business running. The risk level of each of these assets and corresponding data types will have to be approximated and then used to set a threshold that will inform the company's approach towards the risks.
A proper understanding of the organization's risk profile will help choose a compliance framework that suits the company. However, choosing a framework will depend on factors like the scope of coverage, level of detail, and taxonomy. Bear in mind that frameworks only serve as a benchmark, and it is up to the company to decide what works best for them, given the business environment and its security and compliance goals.
Set up controls to comply with cybersecurity standards. Controls are in the form of firewalls, encryption, password policies, etc.
Implement policies and update them as and when necessary. Apart from making documentation easier, having policies and provisions to update them makes it easier to keep up with the regulators' demands on information as to how a company's cybersecurity programs work.
Last but not least, companies will need to monitor and respond to threats constantly. Cybercrime is always evolving, and new attacks tend to be combinations of exploiting earlier vulnerabilities. Such compliance programs must have the capacity to neutralize such threats before they morph into a full-fledged data breach.
The Future of Cybersecurity Compliance
The global pandemic, coupled with sluggish economic activity, resulted in a deluge of data breaches that served as a clarion call for companies and regulators to amp up their cybersecurity approaches. This spike in cybercrime has increased the pace of implementation; having robust cybersecurity compliance measures in place could very well lead to the mushrooming of an entire industry surrounding compliance. Shrinking IT budgets will mean that companies need to have lean and efficient in-house cybersecurity teams instead of outsourcing their compliance activities to third-party organizations.
With global collaboration reaching its peak in 2020, we are bound to witness an increase in globally recognized cybersecurity frameworks that cater to the nuances of multiple industries and the regions they work in. More targeted frameworks, coupled with stricter and more collaborative international enforcement, will aid in erasing borders in the pursuit of identifying and apprehending cybercriminals.
Greater reliance on third-party compliance assessors by regulatory bodies to identify the hot spots that existing regulations don't cover. Businesses will have to be extra cautious about selecting a suitable assessor to ensure maximal compliance.
The emergence of new technologies, especially the introduction of 5G networks, artificial intelligence, and biometric authentication systems, will result in different and more sophisticated attacking patterns, the likes of which companies haven't seen before.
For organizations to be truly resilient in the digital era, they will need to be keyed in existing cybersecurity approaches and emerging trends.
They will have to work actively towards building their capabilities to an appropriate level of maturity by taking definite and discrete steps towards their goals:
- Establish a baseline across all business-critical capabilities
- Conduct a thorough assessment of operations to establish benchmarks and set target maturity levels
- Draw out a plan of action, and prioritize with decreasing order of relevance
- Conduct periodic assessments of capabilities and maturity levels as part of a broader organizational initiative to strengthen the commitment to continuous improvement.
About the Author

Mark Weston is the CRO & Co-Founder of RegulativAI. He has been held a number of CIO roles in tier 1 banks and delivered several global solutions in the cybersecurity, regulatory and compliance domains.
Latest Posts


.jpg)

